When we hear VPN most of the people think of proxying your IP with another regions address.
VPN is generally a Client and Server architecture where we have VPN Servers and VPN Clients. Software which allows client machines to securely connect over the VPN Servers.
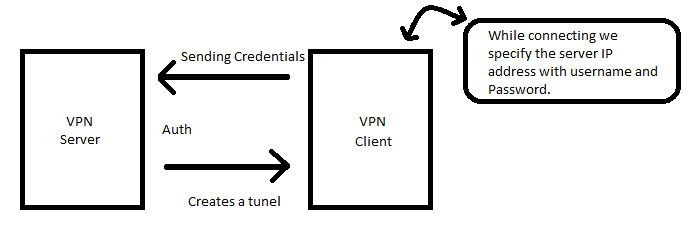
To understand how VPN is more secure we need to understand the mechanism which VPNs follow to make the communication secure and encrypted.
Man In The Middle attack(MITM attack): In cryptography and computer security, MITM attach is where Intermedia Hacker secretly tries to read the data packets which are sent from the source to destination i.e, Server to Victim from the image below.
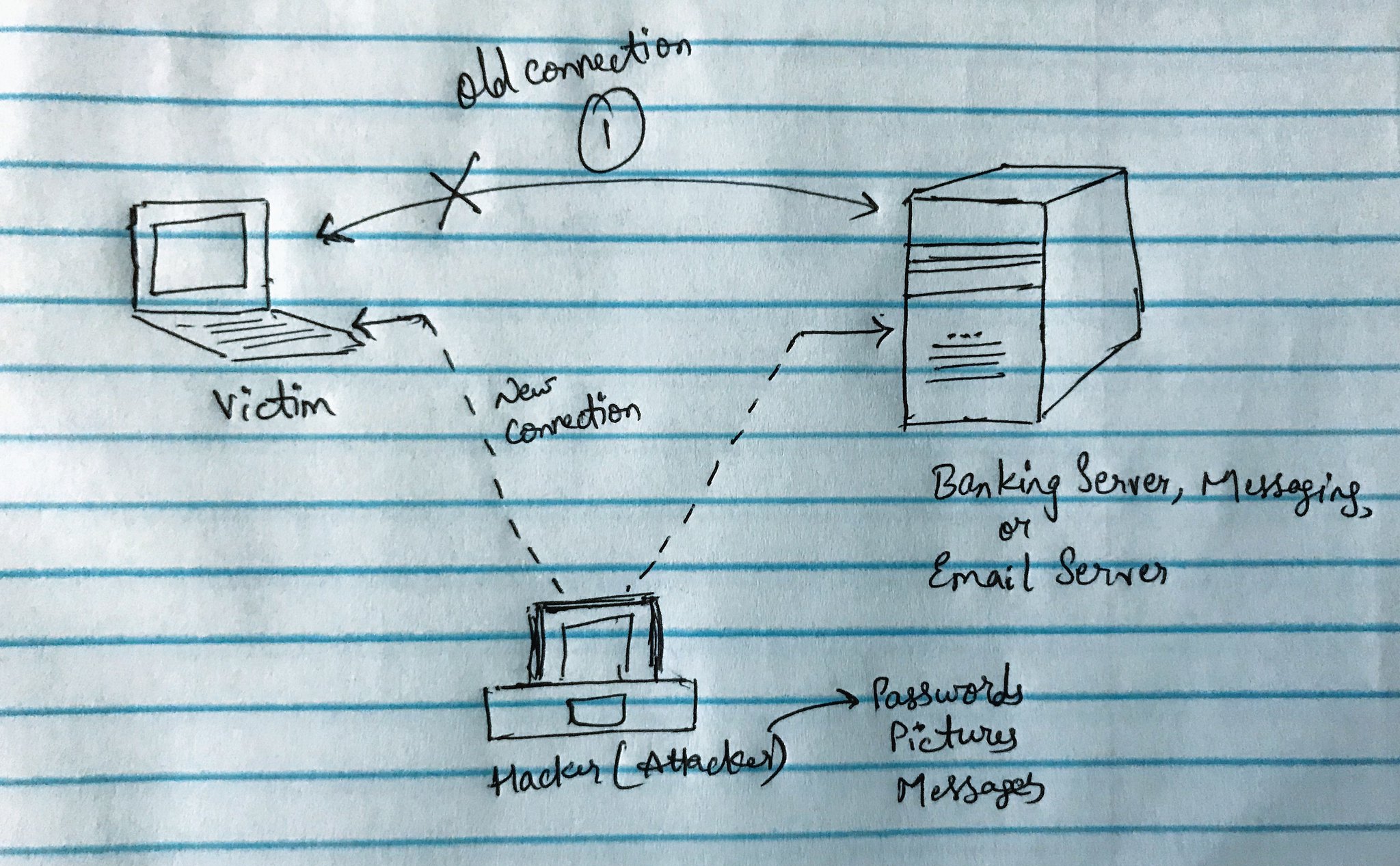
Tunneling Protocol: It creates a tunnel between source-destination an encrypts the data transferred between them.
The tunnel will try to detect the penetration done by hackers & the tunnel will shut down and create an alternate way to reach the destination.
Most tunneling protocols operate at layer 4, which means they are implemented as a protocol that replaces something like TCP or UDP. VPN tunnels allow remote clients to tunnel into our network.
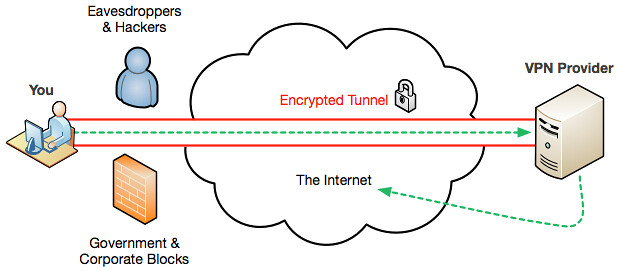
Challenges for VPN:
We have to check the upload connection at destination network where the VPN Server is trying to connect otherwise it will be very slow.